- July 22, 2021
- Posted by: juliaHDG
- Category: Blog

The Critical Need for Data Center Perimeter Security
As the Internet of Things (IoT) continues to grow, an unprecedented amount of business-critical information is being stored into a concentrated data center, exposing new risks.
Even a single data center perimeter security breach can wreak havoc on a company, and by extension, the digital economy itself. Now that cyber security in the form of firewalls and online protection has been generally established, the physical perimeter is the next area of focus for data center security.
Thermal cameras, along with the best practices of perimeter protection, can go a long way towards reducing business loss.
Beyond the risk to the stored data itself, data center organizations face liability and negative perception caused by theft or disruption of services. Additional challenges include ensuring that people are not encroaching onto expansive data center perimeters undetected, and addressing the safety of personnel and the community should outdoor power systems become compromised. The financial impact from the theft of expensive networking and computing equipment remains a concern as well.
Perimeter Security is the First Step in Securing a Data Center
Given the recognition that data centers represent critical infrastructure in the new economy, awareness is growing about the essential need for effective data center perimeter protection. At SightLogix, where our thermal security cameras are used to protect perimeters at data centers throughout the world, we want to ensure that you understand the main components of this often-overlooked requirement, and offer good practices to meet the security requirements.
The 5 Ds of perimeter protection – deter, detect, deny, delay and defend – can form a template for creating a complete perimeter protection strategy. When augmented with detection technology, each layer works to prevent access to your site’s assets and give you time and intelligence to respond to threats effectively.
Deter
The first layer of security is the outermost perimeter. While physical barriers can create a deterrent against perimeter intrusions, the most optimized approach will add an ability to detect intruders as they approach the barrier. This can be best achieved combing a good deterrent with buffer zones of detection that give security teams more time to respond and intercept an event in real time.
Things that help when considering a physical barrier as part of your deter strategy include:
- Placement of fences along the vulnerable areas of the property
- Combining a barrier with a long-range, buffer-zone detection system
- Absence of shrubbery or other barriers to camera line of sight
- Warning announcements, like “No Trespassing” signs
- Winding roads to discourage high speeds
Detect
Because of the critical nature of data centers, missing intruders is unacceptable. While fences and physical barriers can deter intruders, early and accurate detection of an intruder is key. This means consistently monitoring even the most expansive data center perimeter to automatically detect threats with high reliability – no matter the circumstances.
This is where technology can play a role. Solutions like smart thermal cameras have become a popular choice for detecting intruders along data center perimeters because they can see through the dark, bright sun, or bad weather, and deliver accurate alarms with visual details about the nature of an intrusion.
SightLogix’s approach is to utilize our smart thermal perimeter camera SightSensor NS Series, or SightSensor TC Series to provide highly accurate detection of unwanted visitors while ignoring motion from false alarms such as wind or small animals. Intruders that violate video analytic rules immediately trigger an alarm, sending video of the event while alerting the security team to the target’s precise location.
SightLogix smart thermal cameras are also able to detect intruders over hundreds of meters, providing a buffer zone of security over large data center perimeters, providing an accurate, early warning to help form a precise response.
Often these sites employ Pan Tilt Zoom cameras which can be automatically controlled by SightLogix SightTrackers to zoom and track intruders as they move throughout the site in real time for important situational awareness as a break-in unfolds.
With the deployment of deterrents as well as reliable detection, you can greatly enhance your overall perimeter security capability.
Deny
The deny perimeter strategy keeps unauthorized pedestrians out while allowing authorized personnel to enter. This perimeter approach has traditionally included manned security gates at all points of entry, additional checkpoints throughout the facility, multi-factor authentication, biometrics, and even turnstiles to prevent tailgating or piggybacking.
Advancements in geospatial video analytics combined with thermal cameras can also play an important role in the deny strategy as well. These systems can be used to create zones of detection based on size, speed, or bearing, giving you an important tool to control access based on behavior.
For instance, rules can be created that only detect pedestrians moving from the fence towards internal asserts, representing a risk, while ignoring pedestrians leaving the facility, which are not a risk.
Delay
The delay strategy has the sole objective to slow down an intruder enough that the security team has time to respond. This can include physical barriers at the perimeter itself, along with smart cameras that can detect the presence of intruders at a great distance, giving you time to assess and intervene long before the physical building can be breached.
Defend
The final layer of perimeter security, the defend layer is the security team and/or police responding to the intruder and apprehending them. With highly reliable detection matched to real-time visual details, the security team has ample incident response time and important information about the event to ensure your data center is optimally secured.
Regular Audits and Robust Documentation Keep Strategies Up-to-date
All the security measures above won’t matter if your data center personnel do not set up the right protocols and procedures. Ensure that your data center has rigorous employee training, robust documentation of rules, and conducts regular audits. Audits include everything from daily security check-ups to SOC 2 compliance. Also regularly evaluate permissions to make sure that access is only delegated to those that need it as an employee’s needs can change as their role evolves.
SightLogix and Data Center Security
Our clients have turned to SightLogix smart thermal cameras to address data center perimeter challenges for a number of reasons, including:
- Our system’s unmatched analytic detection performance, which detects and acquires an intruder’s speed, bearing, and geo-location in milliseconds – for the fastest preemptive response
- The power of our system to provide early warning of intruders over massive buffer zones beyond the data center walls – detecting intruders outside, inside, and at the perimeter fence – over hundreds of meters far and wide
- Our system’s ability to automatically spin and zoom third-party PTZs to follow a detected target for real-time assessment
- We work directly with our clients and their integrators to develop a complete design solution that uses SightLogix smart cameras to provide comprehensive protection over these important assets.
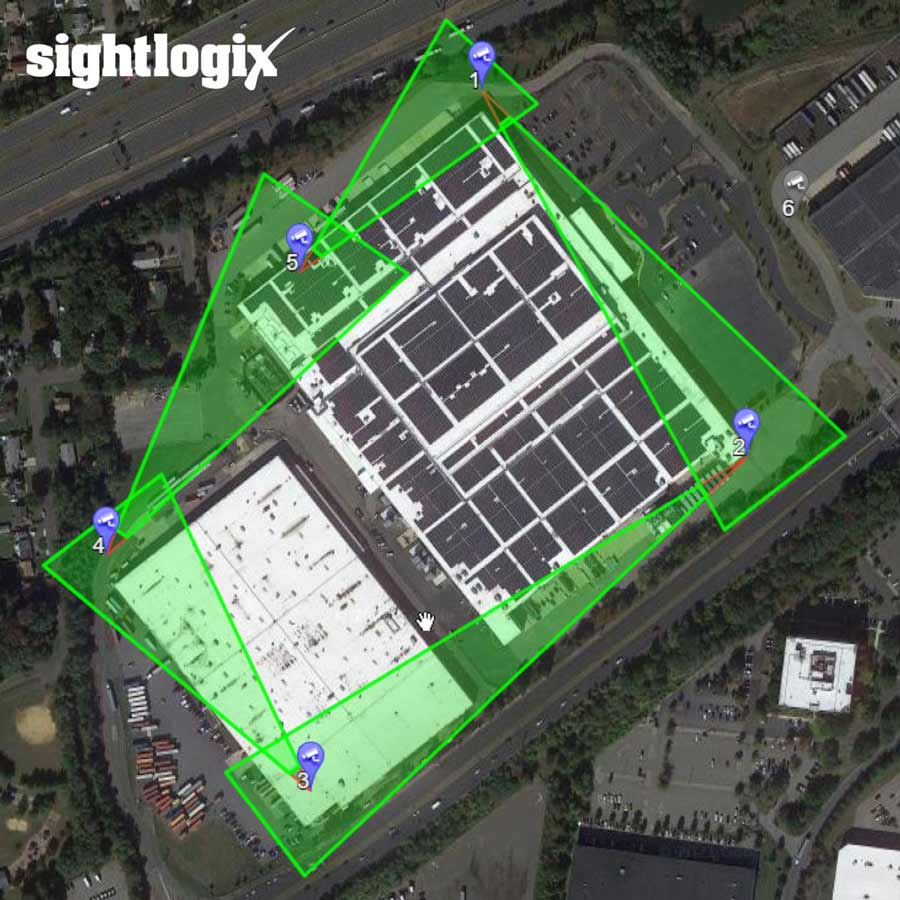
SightLogix Worldwide Data Center Security Customers
SightLogix data center customers include Telecom Italia Mobile (TIM) in Italy, where the smart thermal camera system is used to alert onsite guards the instant an intrusion occurs over their expansive grounds, spanning 57 acres, creating a blanket of awareness around the entire perimeter with many fewer cameras compared to alternatives.
In the US, a major financial trading organization has been using the SightLogix system to address security and safety concerns. Like many data centers, the site is located near a residential area where lighting is either not allowed or not desired, making thermal cameras, which operate in complete darkness, a good choice. The site also utilizes high-voltage step-down transformers to meet power requirements, creating a serious safety risk should someone enter the facility’s perimeter for commonplace reasons like retrieving a thrown ball. For this reason, they needed highly reliable detection with real-time alerts provided by the SightLogix system.
Other data center clients using SightLogix thermal perimeter camera solutions include a federal facility hosting national security resources, and Fortune 10 organizations across the world.




